Unlocking Secrets with Hashcat: Your Ultimate Keymaster
In the ever-evolving landscape of cybersecurity, the ability to decrypt encrypted information is crucial. Hashcat, a powerful open-source password recovery tool, stands as a champion in this realm, offering security professionals a means to unlock encrypted secrets ethically and responsibly.
What is Hashcat?
At its core, Hashcat is a versatile password cracking utility designed to recover lost or forgotten passwords from various cryptographic hashes. Utilizing advanced techniques and algorithms, Hashcat attempts to decipher these hashes and unveil the original plaintext passwords they represent. With a focus on both speed and precision, Hashcat has become an indispensable tool for penetration testers, security analysts, and researchers alike.
Installation and Setup
For windows
To acquire the most recent release of Hashcat, please visit the official repository at https://github.com/hashcat/hashcat/releases. From there, proceed to download the latest version available. Once the download is finished, simply extract the contents of the 7z file. Following these steps, you will successfully set up Hashcat and be ready to utilize its capabilities efficiently.
For linux
Following these commands, you can easily update your system, install the basic version of Hashcat, and, if applicable, install the Nvidia-specific version for optimal performance with Nvidia GPUs
sudo apt update
sudo apt upgrade
# to install the basic version
sudo apt install hashcat
# if you have a nvidia gpu installed, use this instead
sudo apt install hashcat-nvidiaFor MacOS
By executing this command, you can effortlessly install Hashcat on your macOS system, allowing you to utilize its password cracking capabilities and conduct security testing. And latest version support Metal (the replacement of OpenCL in Mac)
brew install hashcatSupported Cryptographic Ciphers
Hashcat supports a wide range of cryptographic algorithms and hashing functions, making it versatile enough to tackle a diverse set of hash types. Some notable ciphers Hashcat can handle include:
- MD5 (Message Digest Algorithm 5): A widely used cryptographic hash function that produces a 128-bit hash value, commonly represented as a 32-character hexadecimal number. While once popular for its speed, MD5 is now considered weak due to vulnerabilities that allow collision attacks.
- SHA-1 (Secure Hash Algorithm 1): Initially designed for secure digital signatures, SHA-1 produces a 160-bit hash value, often represented as a 40-character hexadecimal string. Like MD5, SHA-1 is susceptible to collision attacks and is no longer recommended for security-sensitive applications.
- SHA-256 (Secure Hash Algorithm 256) and SHA-512 (Secure Hash Algorithm 512): Part of the SHA-2 family, these ciphers produce hash values of 256 bits and 512 bits, respectively. They offer significantly stronger security compared to MD5 and SHA-1 and are widely used in modern security protocols.
- bcrypt: An adaptive hashing algorithm designed to slow down brute-force attacks by incorporating a cost factor that can be increased over time. bcrypt is commonly used for securely storing password hashes in databases.
- scrypt: A password-based key derivation function that incorporates memory-intensive operations, making it resilient against attacks that utilize specialized hardware. scrypt is often used for protecting sensitive data, including password hashes.
These ciphers represent just a fraction of the encryption algorithms Hashcat can tackle, making it an indispensable tool for cracking various hash types encountered in real-world scenarios.
As you embark on your journey through the realm of Hashcat, remember the ethical considerations associated with password cracking. Always operate within the bounds of legality and use Hashcat responsibly to enhance security rather than compromise it.
In the upcoming sections, we'll dive deeper into the techniques, strategies, and best practices that Hashcat offers to crack passwords and uncover encrypted secrets.
Basic Hashcat Usage
Hashcat offers a wide range of powerful features for password cracking. Here, we will explore the fundamental aspects of Hashcat usage, dictionary attacks, and brute-force attacks, along with examples to illustrate each technique.
The basic
Hashcat is primarily operated via the command line interface. It provides numerous options to customize and fine-tune the cracking process. These options allow you to specify the hash type, attack mode, input files, and more. For example:
#basic
hashcat [options] hashfile [dictionary]
# An example dictionary attack
hashcat -m 0 -a 0 -o cracked.txt target_hashes.txtIn this command, -m 0 specifies the hash mode (in this case, MD5), -a 0 selects the attack mode (straight), target_hashes.txt represents the file containing password hashes, and -o cracked.txt is the file where the results will be saved.
Hashcat Techniques and Strategies
Unlocking encrypted secrets requires more than just a powerful tool—it demands a strategic approach. Hashcat empowers security professionals with a toolkit of techniques that, when wielded adeptly, can yield successful password recoveries. Below, we explore several key techniques and strategies for making the most of Hashcat's capabilities:
For this section you could use the next password hashes
5f4dcc3b5aa765d61d8327deb882cf99
fe48517a4534e2c7d081d22825247a3b
21e7a7a21c953c3cd373a3cbd5d66a3f
12e04b258ca11263a299d1212357fd16
4d186321c1a7f0f354b297e8914ab240And this are the unencrypted passwords.
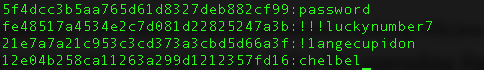
password -> 5f4dcc3b5aa765d61d8327deb882cf99
!!!luckynumber7 -> fe48517a4534e2c7d081d22825247a3b
!1angecupidon -> 21e7a7a21c953c3cd373a3cbd5d66a3f
chelbel -> 12e04b258ca11263a299d1212357fd16
hola -> 4d186321c1a7f0f354b297e8914ab2401. Brute Force and Dictionary Attacks
Brute Force: The brute force approach involves trying every possible combination until the correct password is found. While comprehensive, it can be time-consuming and resource-intensive.
The command used for a MD5 encryption would be the one below, the result will be saved in the file password.txt
hashcat -m 0 -a 3 encrypted.txt -o password.txtAnd when it finish you will find something like this
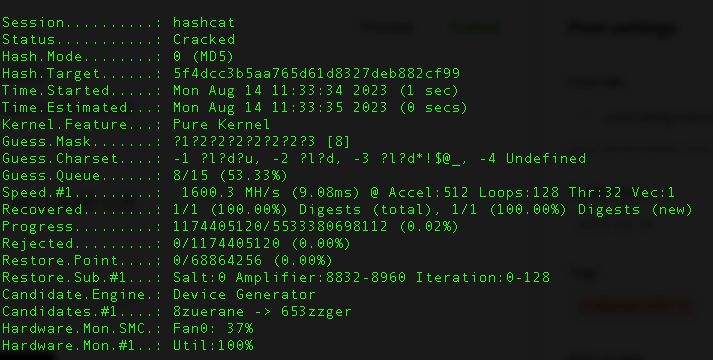
In this case we got the unencrypted password password
5f4dcc3b5aa765d61d8327deb882cf99:passwordDictionary Attacks: Leveraging wordlists containing common passwords and phrases, dictionary attacks narrow down the search space. These attacks are often more efficient and effective, capitalizing on human tendencies to use familiar words.
The command used for a MD5 encryption with a dictionary attack is the one below:
hashcat -m 0 -a 0 encrypted.txt dictionary.txt -o passwords.txt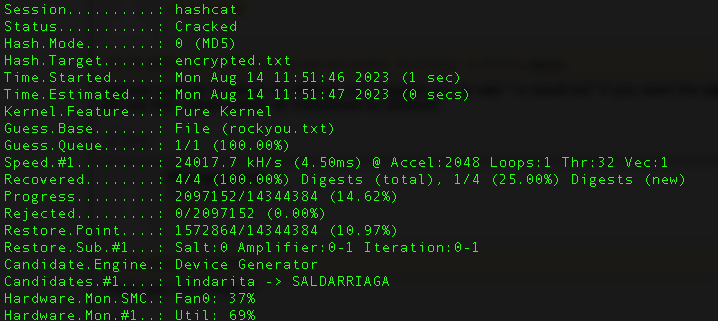
This are the cracked passwords
2. Rule-Based Attacks
Hashcat's rule-based system enhances cracking efficiency by applying transformations to passwords. Rules like appending digits or altering case can expand the search space and increase the likelihood of success.
Crafting Effective Rules
The beauty of rule-based attacks lies in their flexibility. By crafting and fine-tuning rules, you can adapt your attack to the specific characteristics of your target hashes and the patterns often employed by users when creating passwords. Some example rules include:
- Append/Prepend: Adding characters, numbers, or symbols to the beginning or end of words.
- Leet Speak: Substituting letters with numbers or symbols that resemble the letters (e.g., "l33t" for "leet").
- Case Modification: Altering the capitalization of characters within words.
- Character Substitution: Replacing certain characters with similar-looking ones (e.g., replacing "o" with "0").
- Duplicate Letters: Replicating letters within words for added complexity.
The command to use rule based attacks is
hashcat -m 0 -a 0 encrypted.txt dictionary.txt -r custom_rules.rule -o cracked_passwords.txtTo create your custom_rules.rule file we recommend you to check this.
3. Mask Attacks
Mask attacks employ a template to define potential password structures, such as known characters at specific positions. This technique is particularly effective when parts of the password are known.
The command below shows how to perform a mask attack for a password with the length of 4 letters and only letters ?a?a?a?ais the mask, it would work with holafor example.
hashcat -m 0 -a 3 encrypted.txt "?a?a?a?a" -o password.txt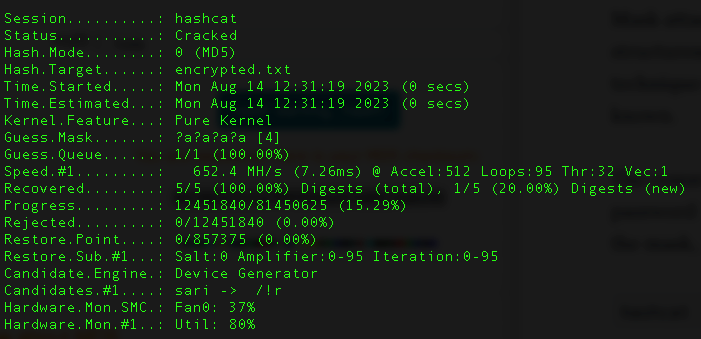
4. Combination and Hybrid Attacks
Combination Attacks: These attacks combine words from dictionaries with various rules to create new password candidates, expanding the search beyond common words.
hashcat -m 0 -a 1 encrypted.txt rockyou.txt mycustomlist.txt -o cracked_passwords.txtHybrid Attacks: By merging elements of different attack modes, hybrid attacks offer a more comprehensive approach to cracking complex passwords.
hashcat -m 0 -a 6 encrypted.txt rockyou.txt -r best64.rule -r leet.rule "?d?d?d" -o cracked_passwords.txt5. Optimizing Attack Modes
When it comes to cracking passwords, selecting the right attack mode in Hashcat can significantly impact your success rate and the time it takes to crack the hashes. Understanding the strengths and weaknesses of different attack modes will help you tailor your approach to the specific hash types and the nature of the passwords you're attempting to crack.
Tips
- Prioritize Likely Candidates: Start with dictionary attacks and rule-based attacks targeting common patterns. These attacks are often faster and more successful in the early stages.
- Use Masks Wisely: For known patterns or passwords with specific characteristics, masks can speed up the cracking process by drastically reducing the search space.
- Custom Rules: Develop custom rules tailored to the specific patterns of your target audience. This can yield impressive results in rule-based and hybrid attacks.
- Leverage Hybrid Approaches: Experiment with hybrid attacks that combine wordlists, rules, and masks to get the best of all worlds.
- Regular Monitoring: Monitor your progress and adapt your attack strategy based on the hashes cracked and the patterns observed.
Remember, there is no one-size-fits-all approach to password cracking. A combination of techniques and a thoughtful selection of attack modes will maximize your chances of success while optimizing your use of resources and time.
6. Wordlists and Dictionaries
Wordlists and dictionaries form the cornerstone of password cracking efforts. These collections of potential passwords provide the material that cracking tools like Hashcat use to match against hashed passwords. Understanding how to choose, create, and enhance these lists is essential for optimizing your password cracking endeavors.
Choosing the Right Wordlists
When selecting wordlists, it's important to consider the context of the target audience. Commonly used passwords, leaked password databases, and even specialized dictionaries related to specific topics (such as sports, movies, or technology) can be valuable. Remember that the more comprehensive and diverse your wordlists are, the better your chances of success.
Creating Custom Dictionaries
While precompiled wordlists are useful, crafting custom dictionaries tailored to your target audience can yield even better results. Start by analyzing common password patterns for the intended user base. Include variations like leet speak, character substitutions, and numbers added to words. These variations mimic real-world password creation behaviors.
7. Performance Optimization
Efficiency is crucial when performing password cracking tasks, as the speed at which hashes are processed directly impacts the time required to crack passwords. Hashcat offers various performance optimization techniques that can help you maximize your cracking speed while making the most of available resources.
Hardware Acceleration
One of the most effective ways to enhance Hashcat's performance is to utilize hardware acceleration, especially through graphics processing units (GPUs). GPUs are highly parallel and can perform hash calculations significantly faster than traditional CPUs. To enable GPU acceleration, ensure your hardware is compatible with Hashcat, install the appropriate drivers, and select the correct device in your command.
hashcat -m <hash_mode> -a <attack_mode> <hash_file> <wordlist> -d <device_number>Optimized Hash Modes
Choosing the right hash mode for your target hashes is crucial. Different hash algorithms require varying levels of computational effort. For instance, GPUs excel at cracking MD5 or NTLM hashes, while bcrypt and scrypt hashes are intentionally designed to be slow. Select the appropriate hash mode using the -m option to optimize your attack.
Tuning Attack Modes
Selecting the most suitable attack mode based on your knowledge of the passwords can dramatically impact performance. Rule-based attacks (mode 6) are efficient when patterns like leet speak or character substitutions are common. Combining modes, such as using hybrid attacks, can balance brute force with dictionary-based approaches, making your attack more efficient.
Mask Attack Precision
When using mask attacks, crafting an effective mask can greatly reduce the search space and improve performance. Precisely define the pattern and length of the passwords you're targeting to avoid unnecessary computations. Experiment with masks that reflect the expected password format while avoiding overly complex masks that can slow down the attack.
Wordlist Selection
Choosing the right wordlist can significantly impact performance. Precompiled wordlists like "rockyou.txt" are commonly used, but they can also slow down the attack due to their size. Consider using targeted wordlists that match the demographics of your target audience. Smaller, more relevant wordlists can increase efficiency by avoiding unnecessary attempts.
Parallel Processing and Threads
Hashcat allows you to leverage multiple CPU cores and GPUs for parallel processing. Adjust the number of threads and devices using the -t and -d options to maximize resource utilization. Keep in mind that using too many threads or devices can lead to diminishing returns due to contention for system resources.
Memory Management
Hashcat's performance heavily depends on memory access speed. Ensure your system has sufficient RAM, and adjust Hashcat's memory usage using the -w option. Larger memory allocations might speed up the process but can also lead to stability issues if not managed properly.
Monitoring and Experimentation
Regularly monitor your cracking progress and performance metrics using Hashcat's built-in status updates. Experiment with different combinations of attack modes, rules, masks, and devices to find the optimal configuration for your specific situation.
Optimizing performance in password cracking is a balance between selecting the right hardware, attack modes, and configurations. By leveraging hardware acceleration, fine-tuning attack parameters, and using efficient wordlists, you can significantly reduce cracking time while maximizing your chances of success. Always ensure you're operating within legal and ethical boundaries and have proper authorization for your actions.
8. Ethical Considerations
Password cracking, while a legitimate and useful cybersecurity activity in certain contexts, requires careful adherence to ethical guidelines to ensure that it is conducted responsibly, legally, and with the utmost consideration for the rights and privacy of individuals.

Legal Authorization
Before conducting any password cracking activities, ensure that you have explicit legal authorization to do so. Unauthorized attempts to crack passwords, even with good intentions, can lead to legal consequences and violations of computer crime laws. Obtain written permission from system owners or relevant authorities before proceeding.
Consent and Privacy
Respect individual privacy and consent. Only perform password cracking on systems, networks, or accounts where you have the explicit authorization to do so. Password cracking activities that invade privacy, breach terms of service, or violate user agreements are ethically unacceptable.
Data Protection
Be vigilant about data protection and data security. Do not engage in password cracking on systems that contain sensitive or confidential information without proper authorization. The potential risk of exposing sensitive data through a breach resulting from password cracking underscores the importance of ethical behavior.
Responsible Disclosure
If you discover vulnerabilities or weak passwords during your password cracking activities, follow responsible disclosure practices. Notify the system owners or administrators about the vulnerabilities you've identified so that they can take appropriate action to improve security.
Usage of Cracked Information
If you succeed in cracking passwords, exercise caution and responsibility in how you use the cracked information. Do not misuse passwords to gain unauthorized access to systems or accounts. The primary purpose of password cracking should be to demonstrate vulnerabilities and promote security improvements.
Educational and Professional Contexts
In educational and professional contexts, password cracking can be used as a learning tool to understand vulnerabilities and reinforce the importance of strong security practices. However, these activities should be conducted within a controlled environment and with proper oversight.
Third-Party Services and Data
When using third-party services or data sources to inform your password cracking efforts, ensure that you have the right to access and use that data. Respect copyright, terms of use, and intellectual property rights associated with the data sources.
Ethical Hacking
If you are engaging in password cracking as part of ethical hacking, penetration testing, or cybersecurity research, adhere to industry standards and best practices. Follow the guidelines set forth by reputable organizations and ensure that your actions align with the principles of responsible disclosure.
Professional Conduct
As a practitioner of password cracking, maintain a high standard of professionalism. Engage in open discussions, share knowledge responsibly, and contribute positively to the information security community. Uphold ethical behavior in your interactions with peers, colleagues, and the broader public.
Remember that ethical considerations are paramount in any cybersecurity activity. While password cracking can be a valuable tool for identifying weaknesses and improving security, it must be approached with integrity, respect for privacy, and a commitment to lawful behavior.
9. Real-World Examples of Hashcat's Practical Applications
a. Cybersecurity Research and Penetration Testing
In the field of cybersecurity, professionals use Hashcat for ethical hacking, penetration testing, and vulnerability assessment. By simulating real-world attacks, researchers can identify weak passwords, test security defenses, and help organizations strengthen their digital fortifications. Hashcat's versatile attack modes and customizable rules make it an invaluable tool for assessing the security posture of systems and networks.
b. Password Recovery and Digital Forensics
Law enforcement agencies and digital forensics experts use Hashcat to recover passwords from seized devices and encrypted files. This aids in accessing evidence, solving cases, and ensuring justice is served. The ability to employ various attack modes and rules increases the likelihood of successfully recovering passwords even from complex and well-protected sources.
c. Security Awareness Training
Educational institutions and organizations use Hashcat in security awareness training programs to demonstrate the importance of strong passwords. By showing employees or students how easily weak passwords can be cracked, organizations can foster a culture of security-conscious behavior and encourage the use of robust password practices.
d. Assessing Cloud Security
As more data migrates to cloud platforms, ensuring the security of cloud-based accounts becomes paramount. Hashcat can be employed to evaluate the strength of user passwords and highlight potential vulnerabilities in cloud service configurations. By proactively identifying and rectifying weak passwords, organizations can mitigate the risk of unauthorized access to cloud resources.
e. Identifying Weaknesses in Legacy Systems
Legacy systems often harbor outdated security practices that can be exploited by attackers. Hashcat aids in assessing the passwords used in these systems, helping organizations identify potential entry points for malicious actors. This enables them to prioritize modernizing security measures and safeguarding valuable assets.
f. Researching Password Creation Behaviors
Researchers in the field of psychology and human behavior have used Hashcat to analyze patterns in password creation. By analyzing cracked passwords, researchers gain insights into common password practices, such as the prevalence of dictionary words, character substitutions, and predictable patterns.
g. Security Policy Enforcement
Organizations can leverage Hashcat to enforce password policies. By cracking passwords within their own environment, organizations can identify users who are not adhering to password complexity requirements. This information can then be used to educate users about proper password practices and drive compliance with security policies.
h. Testing Hardware and Performance Benchmarks
Hashcat's utilization of hardware acceleration makes it a valuable tool for testing the performance and capabilities of CPUs and GPUs. Researchers and hardware enthusiasts use Hashcat to benchmark hardware and evaluate how different components impact cracking speeds. This information helps inform hardware purchasing decisions for security professionals and enthusiasts alike.
i. Verifying Password Hash Strength
Organizations can use Hashcat to verify the strength of password hashes before they're deployed. By attempting to crack test hashes using various attack modes, organizations can ensure that their password storage mechanisms can withstand common cracking attempts, ensuring better protection of user credentials.
j. Academic and Research Projects
Hashcat is utilized in academic settings and research projects to explore various aspects of cryptography, security, and password practices. Researchers study Hashcat's effectiveness in cracking various hash algorithms, develop novel attack strategies, and contribute to the broader field of cybersecurity.
