Nessus: Your Digital Sherlock Exposing Vulnerabilities
Just as Sherlock Holmes meticulously unraveled mysteries with sharp observation and unerring logic, so does Nessus, a remarkable vulnerability scanning tool, navigate the intricate web of networks and systems to expose hidden weaknesses, armed with precision and expertise, embarking on a mission to uncover vulnerabilities that could threaten the very fabric of your cybersecurity defenses. In this exploration, we delve into the intriguing world of Nessus, unveiling how it assumes the mantle of a modern-day detective to safeguard your digital domains.
Unveiling Nessus: Your Digital Sherlock
In the ever-shifting world of cybersecurity, we've got a new detective on the block – Nessus. Think of it as the digital version of Sherlock Holmes, prowling the virtual streets for vulnerabilities instead of clues.
Just like the legendary detective, Nessus is all about meticulous observation. It's like having a magnifying glass for your networks, servers, and apps. It sniffs out the faintest signs of trouble, piecing together the puzzle of potential threats, just like Holmes untangling complex cases.
But Nessus doesn't stop at pointing out problems. It's a protector too, sounding the alarm on vulnerabilities that might otherwise go unnoticed. It's like having your own digital bodyguard.
So, as we dive into Nessus' world, we'll uncover its methods, draw parallels to Sherlock's tactics, and see how it keeps your digital turf safe. Imagine Nessus as that savvy friend who's got your back in the realm of ones and zeros. Ready to explore more? Let's get into the nitty-gritty.
The Role of a Vulnerability Scanner
In the realm of cybersecurity, vulnerabilities aren't just weak spots – they're potential gateways for trouble. Imagine them as open windows in a locked house. And just like you'd want a vigilant guard checking for unlocked windows, that's where vulnerability scanners like Nessus step in.
Think of a vulnerability scanner as your digital inspector, combing through your systems like a hawk-eyed detective. Its mission: to find those weak spots before anyone else does. These weak spots, or vulnerabilities, are like the chinks in your armor, waiting to be exploited by cybercriminals.
By pinpointing vulnerabilities, Nessus does more than just alert you. It empowers you to act, like a heads-up that someone's trying to pick your lock. It's all about nipping trouble in the bud.
But why the fuss? Well, vulnerabilities can lead to data breaches, downtime, and headaches. Like a small leak that can sink a ship, even a tiny vulnerability can have far-reaching consequences in the digital realm.
So, as we venture deeper, let's uncover the behind-the-scenes work of vulnerability scanners and how Nessus, your digital guard dog, keeps those virtual windows locked tight. Ready to dive in? Let's roll.
Installing Nessus: Getting Your Digital Sherlock Online
Time to set the stage for Nessus, your digital detective. Just like bringing in a private investigator to solve a case, you'll need to get Nessus up and running to work its cybersecurity magic.
So, how do you do it? Well, it's as simple as downloading and installing software, that you could find here, you could try it for free after signing for the trial period.
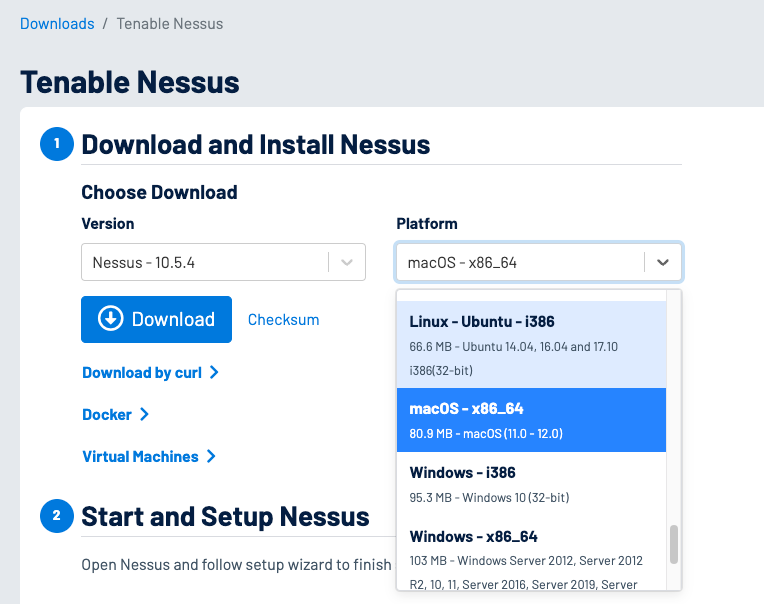
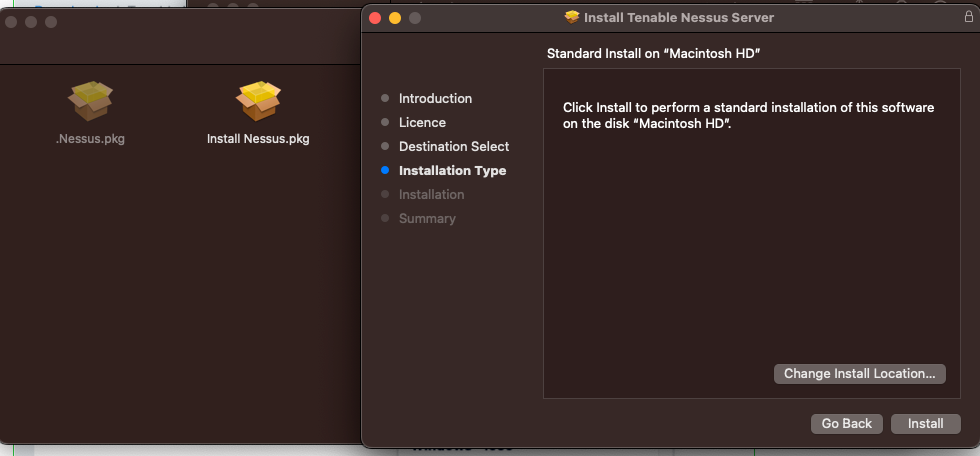
After you could just install it following the setup manager.
And when it is ready it automatically will open in your browser.
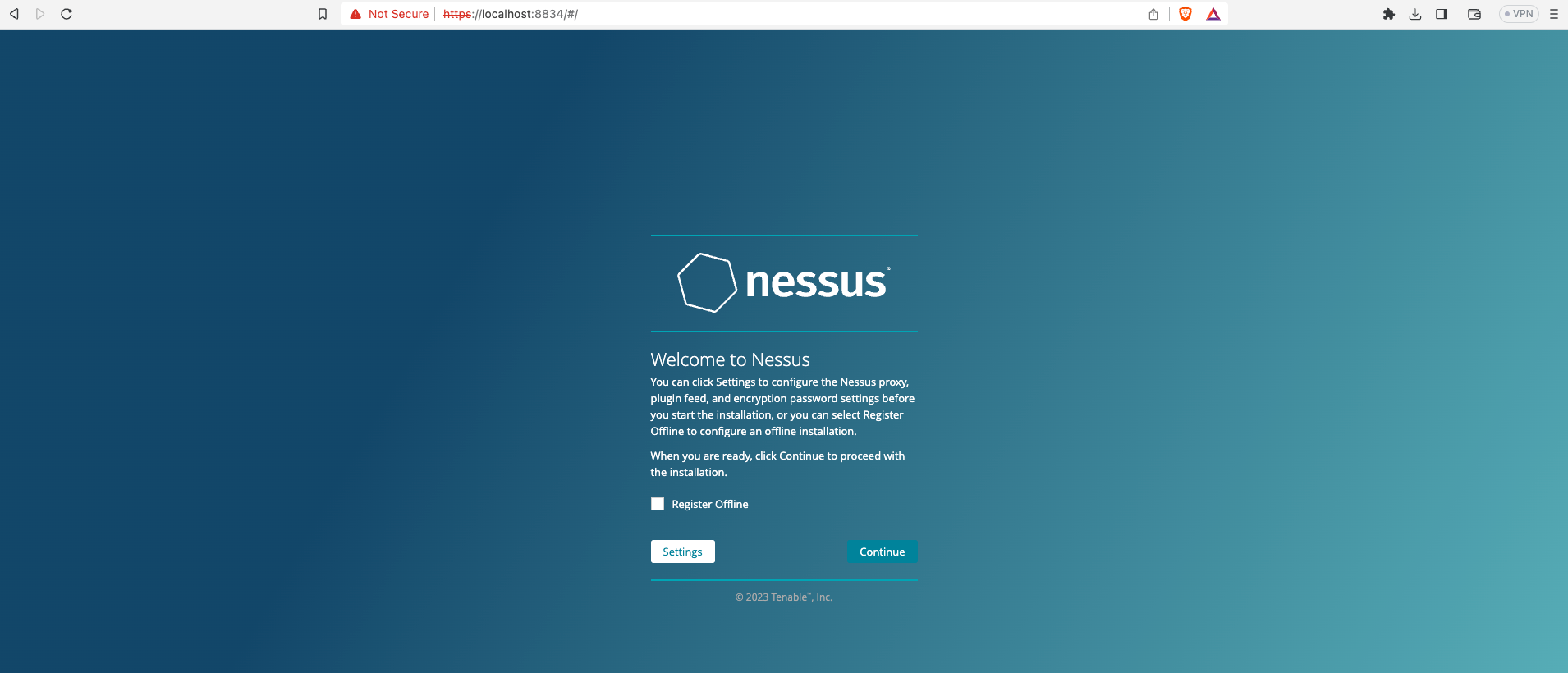
Press continue and introduce you information to start the trial.

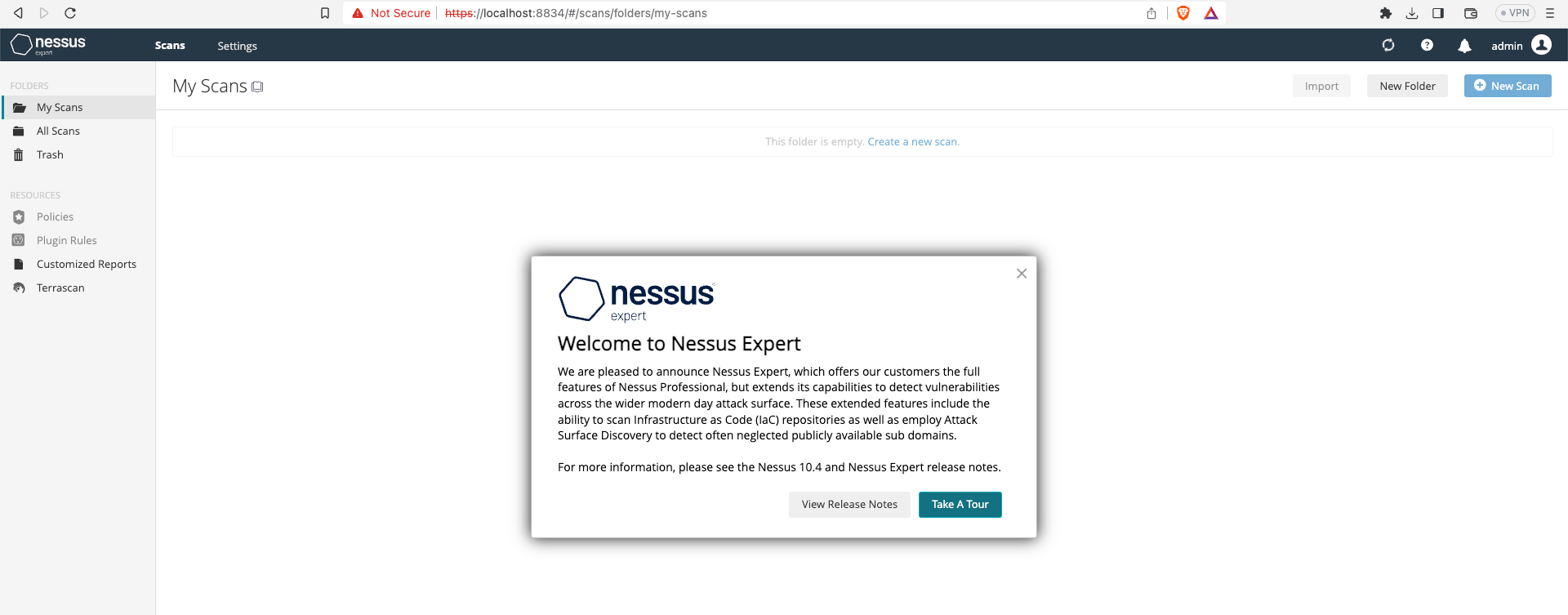
After that create your username and password

And it will start to initialize, wait a few minutes it could take some time.

And then you are ready to go.
Precision in Uncovering Vulnerabilities
Time to dig into the nitty-gritty – how Nessus nails vulnerabilities like a pro detective. Think of it as Nessus having a magnifying glass and Sherlock's intuition rolled into one.
Nessus doesn't just catch vulnerabilities; it's like a heat-seeking missile for weak spots. Imagine it as that friend who spots the tiniest detail that no one else notices.
So, how does it pull off this stunt? Nessus isn't just scanning; it's cross-referencing its vast knowledge. It's like having a buddy who's read all the cheat sheets and knows every trick in the book.
But here's the cool part: Nessus doesn't just do this by the book. It's like a detective tailoring its investigation to your situation. It knows your setup, your quirks, and where the bad guys might strike.
And it doesn't flood you with info either. Like your best buddy, Nessus tells you what needs attention ASAP and what can wait till later.
The Methodology: Nessus vs. Sherlock Holmes
Alright, time for the showdown – how does Nessus stack up against the legendary Sherlock Holmes? It's like comparing two brilliant minds, each with its own unique approach to cracking mysteries.
Imagine Nessus as the digital detective and Sherlock as the classic investigator. Both are all about methodical analysis, but they're working in different realms.
Sherlock, with his razor-sharp mind, pieces together clues and reads between the lines. Nessus does something similar, but it's sifting through code and configurations instead of magnifying glass clues.
Where Sherlock's power lies in deduction, Nessus shines in automation. It's like the difference between solving a puzzle piece by piece versus having a supercomputer that pieces it all together in seconds.
But here's the twist – Nessus isn't limited by human attention span. It can scan huge networks and systems without breaking a sweat. It's like Sherlock having a hundred Watsons to help him analyze cases.
In a way, Nessus takes Sherlock's methodology and supercharges it with digital prowess. It's the next evolution of detective work, tailored for the complexities of the cyber age.
Practical Application: How to Use Nessus
Now that you've got Nessus on board, let's unleash it in the digital wild – just like setting a trained hound to follow a scent. It's all about making the most of your digital Sherlock.
Think of Nessus like your favorite gadget – it's got buttons to press, settings to tweak, and mysteries to uncover. But don't worry, it's not rocket science; it's more like using your smartphone.
Vulnerability Scan in Action: Unmasking Digital Threats
Alright, it's time to see Nessus, your digital Sherlock, in action with a real-life vulnerability scan. Think of this as a ride-along with your detective buddy as they unravel a case.
Step one: You fire up Nessus, your trusty detective. It's like setting a loyal dog on the scent. You give Nessus a mission – scan your servers, apps, and network for any weak points that might be exploited by cybercriminals.
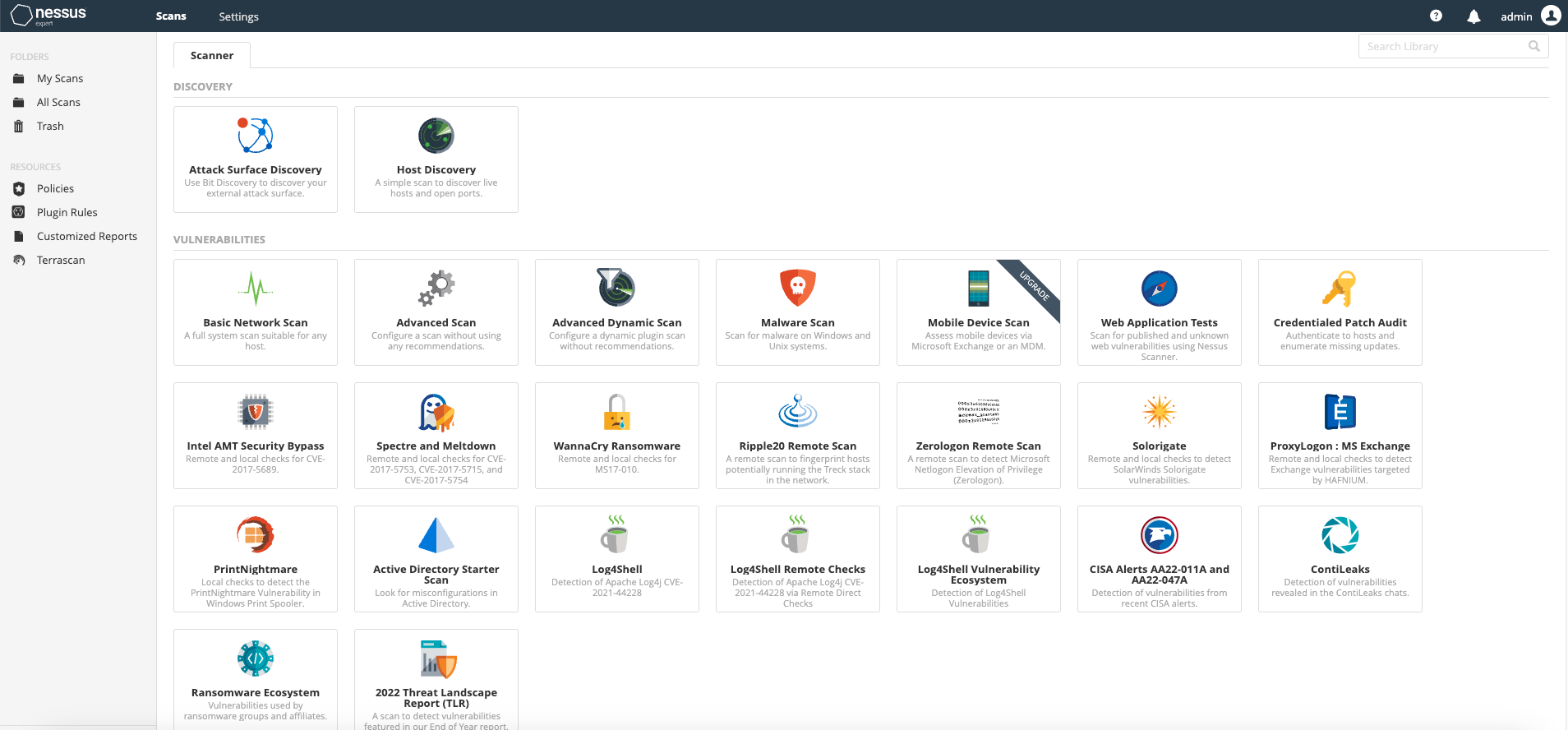
Step two: From the variety of template scans available, we'll select the "basic network scan" for this example. However, feel free to choose any of these templates that catch your interest.

Step three: In the following step, make sure to input a scan name for future identification purposes, as well as the IP address that the scan will target.
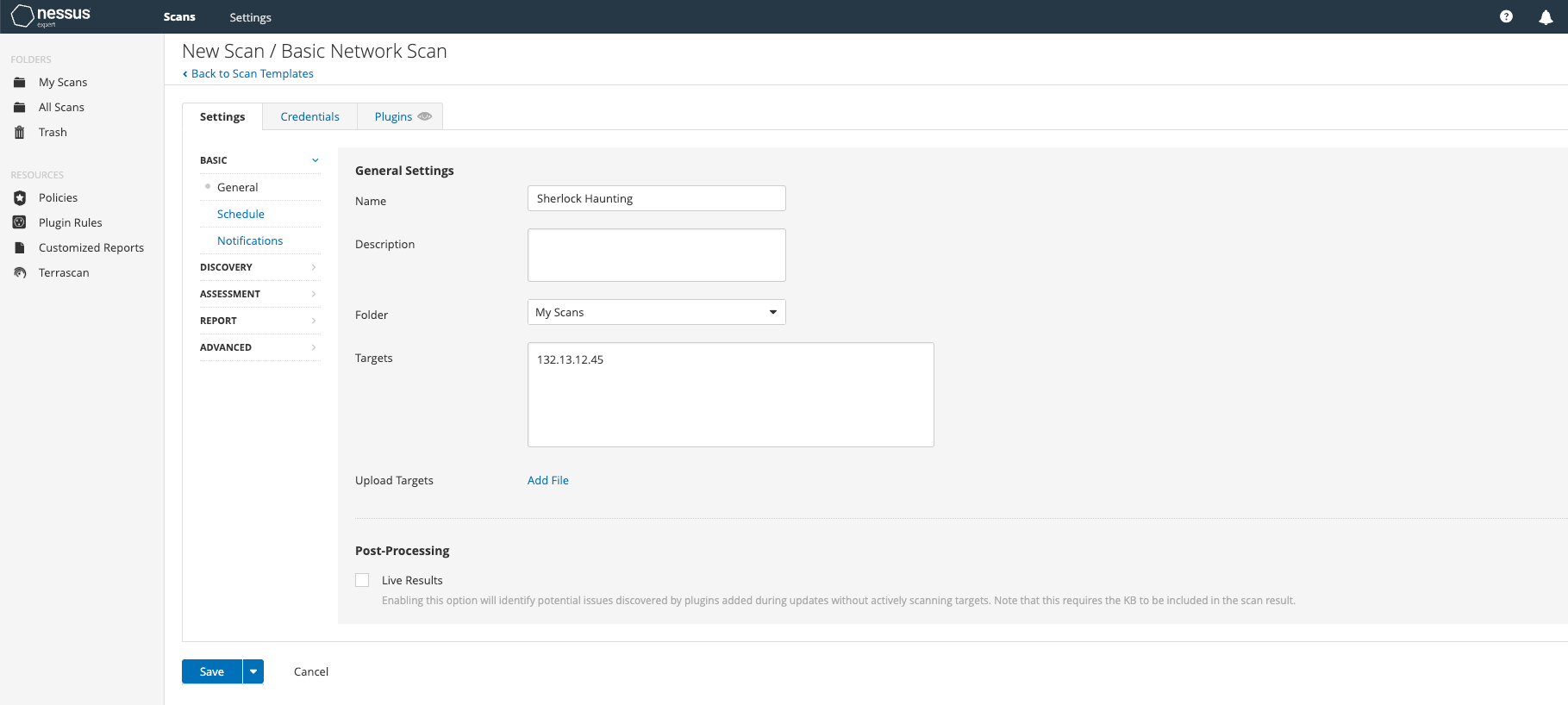
Simply click on the "Save" button, and you will be directed to the following screen.
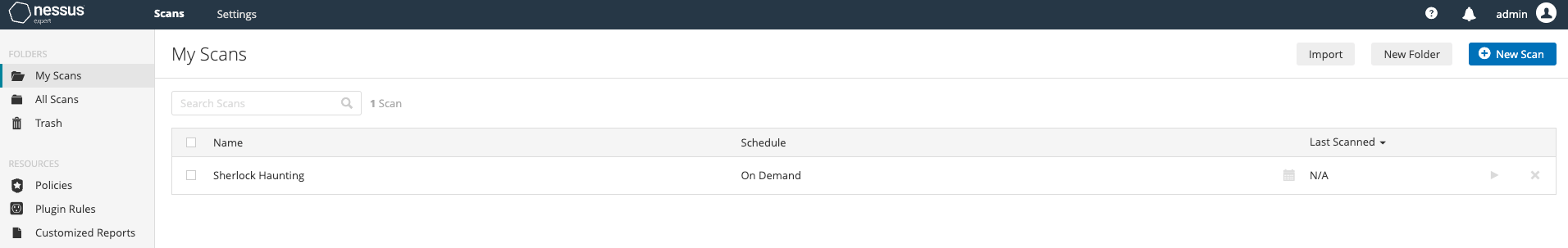
Step four: Click the "Launch" button and await the outcomes.
Step five: Once it's ready, click on it to access the information and it would open the summary.
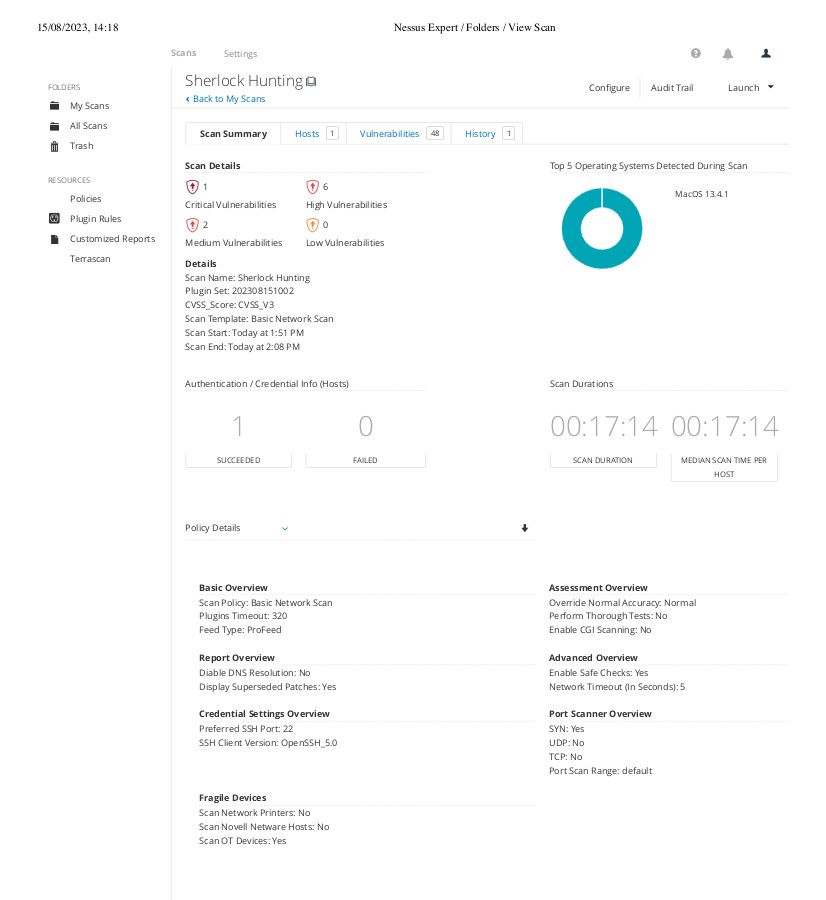
Unraveling the Findings: Making Sense of It All
As you dive into the results, remember – Nessus has your back. It's like that friend who's got a knack for solving stuff. In the next sections, we'll guide you through the vulnerability report, show you how to size up the seriousness, and help you decide what to tackle first. Ready to play cyber detective? Let's go and decode those results!
Alright, let's crack open the treasure chest of info Nessus dug up – time to understand what's going on. Think of this as your decoder ring for the digital secrets Nessus uncovered.
Under the "Host" tab, you'll discover the vulnerabilities detected on each individual IP address.
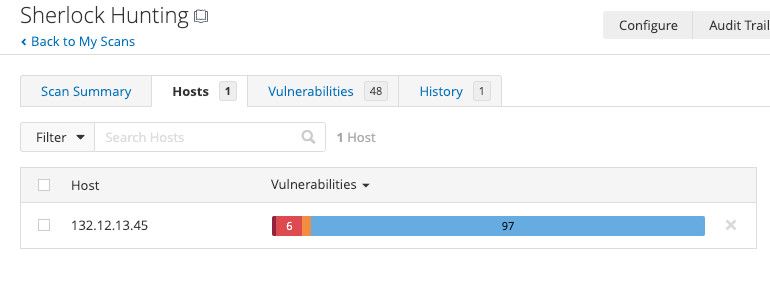
And this summary gives you an idea of the distribution of vulnerabilities detected by Nessus.
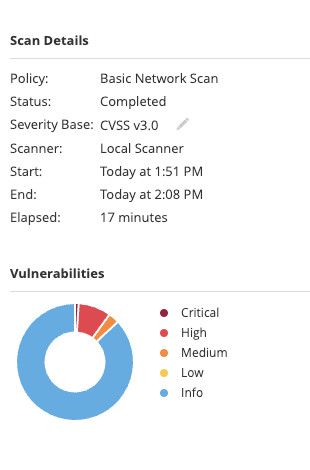
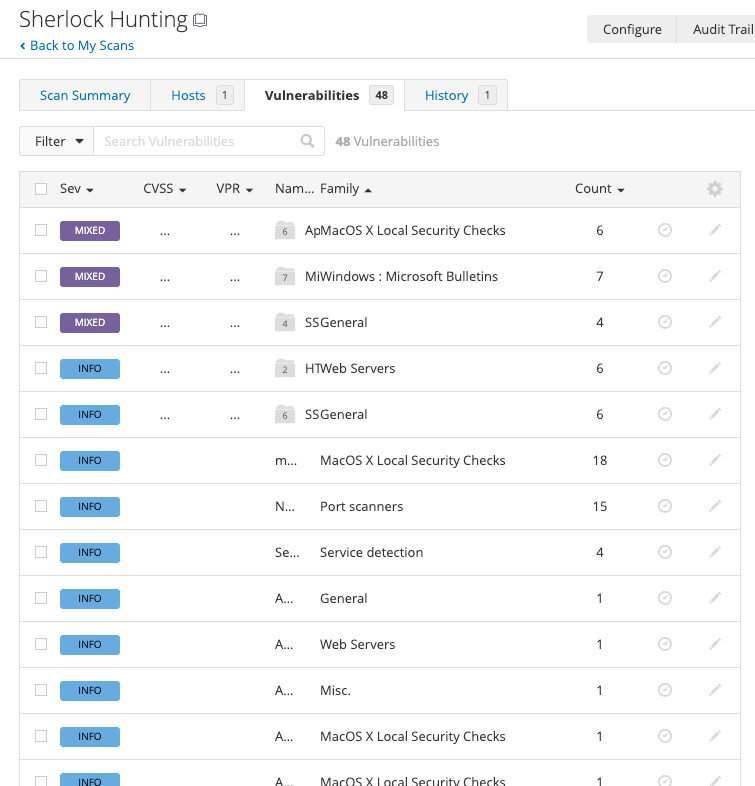
Time to dig deeper? Just swing by the "Vulnerabilities" tab – it's where the real nitty-gritty hangs out.
So, imagine you're at the detective's desk, scan results spread out like a case file. Every vulnerability Nessus found spills its secrets here, like your own set of digital clues.
Each vulnerability gets its moment in the spotlight – name, severity, and a snappy summary. It's like you're reading the juicy bits of a mystery novel – who's involved and what's at stake.
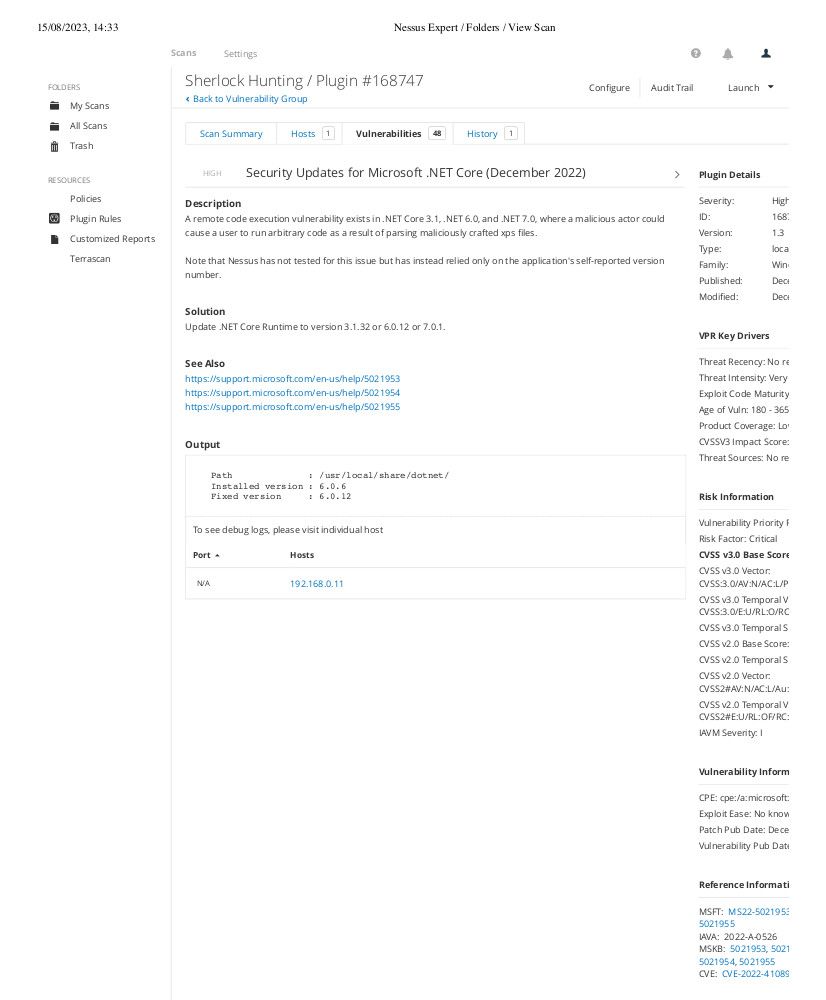
But hold on, we're not stopping at the surface. Click on a vulnerability, and it's like zooming in for a closer look. Nessus spills the beans on how bad this vulnerability could be and what it might let the bad guys do.
And guess what? Nessus isn't a buzzkill that just points out problems. Nope, it's your digital buddy with solutions. It's like your detective friend saying, "Hey, I found this mess, but here's how you can clean it up."
Step six: Time to roll up your sleeves and give those vulnerabilities a run for their money. It's like you're the superhero sweeping in to save the day – but instead of a cape, you've got a keyboard and some tech know-how. Let's dive into action and show those vulnerabilities who's boss!
Conclusion
And there you have it – the adventure through the world of Nessus, your digital Sherlock, comes to a close. It's like wrapping up an exhilarating case with your trusty detective by your side.
Nessus isn't just a tool; it's your cybersecurity sidekick, sniffing out vulnerabilities and uncovering digital mysteries. It's like having a guardian angel watching over your digital kingdom.
As we bid adieu, remember that Nessus is your ally against the ever-evolving threats of the digital landscape. It's your virtual detective, always on the lookout for trouble.
So, it's time to unleash Nessus, your very own digital Sherlock. Armed with precision, insight, and a dash of tech magic, Nessus is here to keep your digital realm safe and sound. Ready to step into the world of cybersecurity with your new detective by your side? Let's go and conquer the digital frontier together!
